Fixing Typos and Breaching Microsoft’s Perimeter
Progressing through certifications, developing as a red teamer, breaking into Bug Bounty — many steps along my security journey have been difficult. One of the easiest things I’ve done was breach Microsoft’s perimeter. Two weeks before compromising a domain-joined Microsoft server, former coworker Adnan Khan discovered a critical supply chain vulnerability in GitHub’s Runner Images.…
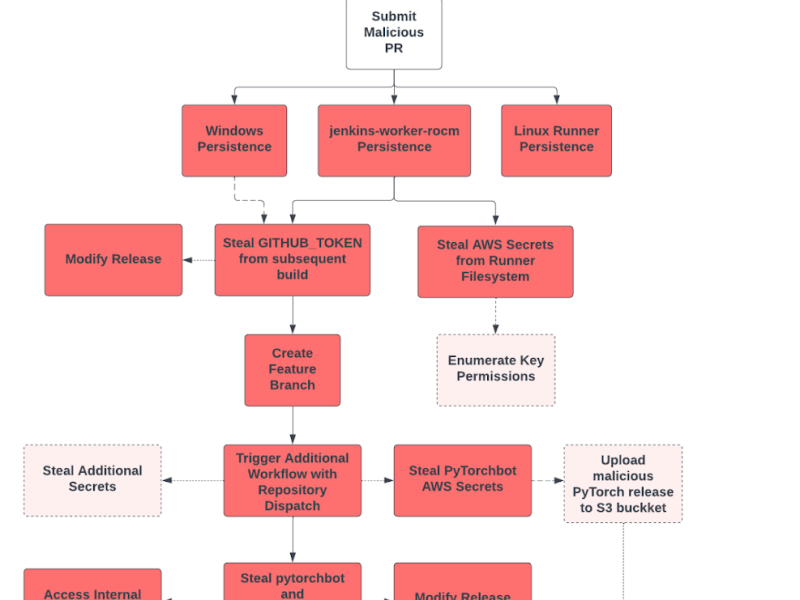
Playing with Fire – How We Executed a Critical Supply Chain Attack on PyTorch
Security tends to lag behind adoption, and AI/ML is no exception. Four months ago, Adnan Khan and I exploited a critical CI/CD vulnerability in PyTorch, one of the world’s leading ML platforms. Used by titans like Google, Meta, Boeing, and Lockheed Martin, PyTorch is a major target for hackers and nation-states alike. Thankfully, we exploited…
Worse than SolarWinds: Three Steps to Hack Blockchains, GitHub, and ML through GitHub Actions
Six months ago, my friend and colleague Adnan Khan started researching a new class of CI/CD attacks. Adnan grasped the significance of these attacks after executing them against GitHub to gain total control of the GitHub Actions runner images. GitHub’s bug bounty program scored this vulnerability as “Critical” and paid a $20,000 reward. Following this…